With exponential growth in cloud technology and the mobile workforce, the corporate network perimeter has been redefined. The traditional perimeter-based security approach is found to be ineffective as the resources are hosted in multi-cloud and hybrid scenarios. Today, organizations need a new security model that can provide secure access to their resources, irrespective of where they are accessed from and regardless of user or application environment. A Zero Trust security model helps in embracing the mobile workplace and helps in protecting identities, devices, apps, and data wherever they are located.
The Zero Trust model operates on the principle of “trust no one, verify everything, every time.” This means that all users, devices, applications, and data that flow within an organization’s network should be verified explicitly before being granted access to resources:
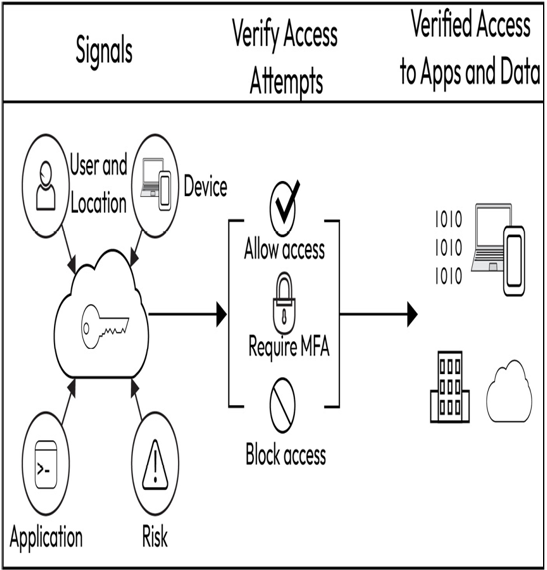
Figure 1.8 – The Zero Trust model (https://www.itgovernance.co.uk/blog/wp-content/uploads/2015/07/PPT-Diagram-Blog.png)
Zero Trust guiding principles
The Zero Trust model has three principles based on NIST guidelines:
- Verify explicitly: The “verify explicitly” principle of Zero Trust means that access should be granted only after a user or device’s identity and security posture have been verified and authenticated. This requires the use of strong authentication mechanisms, such as MFA, that require users to provide additional forms of authentication beyond just a password, such as a fingerprint scan, facial recognition, or a one-time code. In the case of devices, they must be assessed and verified before they are granted access to resources within an organization’s network. This involves evaluating the device’s security posture to ensure that it meets a minimum set of security standards, such as having the latest security patches, running up-to-date antivirus software, and having strong passwords or other authentication mechanisms in place. Devices that do not meet these security standards are either denied access or granted limited access until they can be remediated and brought up to the required security standards.
- Least privilege access: Least privilege access refers to Just-in-Time (JIT) access, which means elevating the permission as and when required to perform some tasks and then bringing back the default access with Just Enough Administration (JEA) to perform day-to-day tasks.
- Minimize the blast radius: This refers to the assume breach mindset, where you build your defense while keeping the worst-case scenario in mind so that even if some external or internal breach occurs, there is a minimum impact on the organization. Network segmentation, end-to-end encryption, advanced threat detection, and deeper analytics visibility are some practices to minimize the blast radius.
These guiding principles help us in understanding the baseline on which we define the conditions for the Zero Trust model. Now, let’s understand which guidelines apply to which pillars.
